And so we enter the new year with some old, familiar problems: The war in the Ukraine rages on, instability in the Middle East persists, protests strengthen within Iran, there is large-scale confrontation and brinkmanship between China and the United States, and instability worsens with the polarization of society within America.
By all accounts, these factors and more suggest that information wars’ manipulation and influence on public consciousness and individuals will only escalate & intensify.
Naturally, with this progression, the methods and means in which information wars are carried out will continue to evolve and intensify.
Considering the setbacks that Moscow now faces in the field of battle, and as the possibility of defeat looms above the Kremlin, it is a safe presumption in our opinion, that Moscow will intensify and increase its already significant efforts and activities in the field of information warfare. This effectively exerts psychological influence over individuals, entities, and societies as a whole, and there is no sign that this modern trend of influence will reverse any time soon. The key is to curtail and implement comprehensive defenses against such antagonistic behaviors, but this requires informed action and reaction. Unfortunately, the West seems vastly under-informed and even those in positions that should be most prepared to advise on the matter seem to lack a comprehensive understanding of the capabilities of the “Russian information counteraction infrastructure.” To ignore the threats posed by malicious Russian information activity is a luxury we simply cannot afford as the threat of significant and widespread destabilization increases.
In both the Soviet era and under Putin’s present day rule, Russian information operations are not considered ancillary or secondary to combat; in fact, Moscow considers this targeted activity as a fundamental part of general warfare in their push to enhance their tactical and strategic supremacy over others.
A further complication in addressing and assessing the infrastructure of “Russian Information operations” has been caused by naivety, as certain Journalists & Researchers (even in the U.S.) have in many cases, unwittingly perpetuated propaganda distributed by RT and Sputnik. Additionally, less conspicuous disinformation and manipulations are being overlooked (partly because this disinformation is deeply entrenched in seemingly credible resources, and the people responsible for unwittingly distributing & perpetuating this disinformation further are not educated in rooting out hidden propaganda).
This subtle manipulation over otherwise trained ethical researchers and journalists ultimately plays into the hands of the Kremlin and allows a cover-up of the true scale & depth of its activities.
While some Western researchers actively study RT and Sputnik news reports, Russian intelligence agencies continue to explore the possibilities of pushing the boundaries and increasing the effectiveness of the battle in the psychosphere.
In considering the main threats to US national security in the information field in 2023, Russia of course, stands tall, though China and Iran warrant specific mention too. Although both of these countries have, over the past two decades, invested heavily in the creation and improvement of their own respective informational and psychological combat infrastructure, they still largely rely on the Russian model. It is evident that the bulk of these techniques and methods employed by Beijing and Tehran against the United States and its allies have been borrowed from Moscow.
Thus, the Russians could be considered pioneers and trailblazers for all other malicious actors who target the United States.
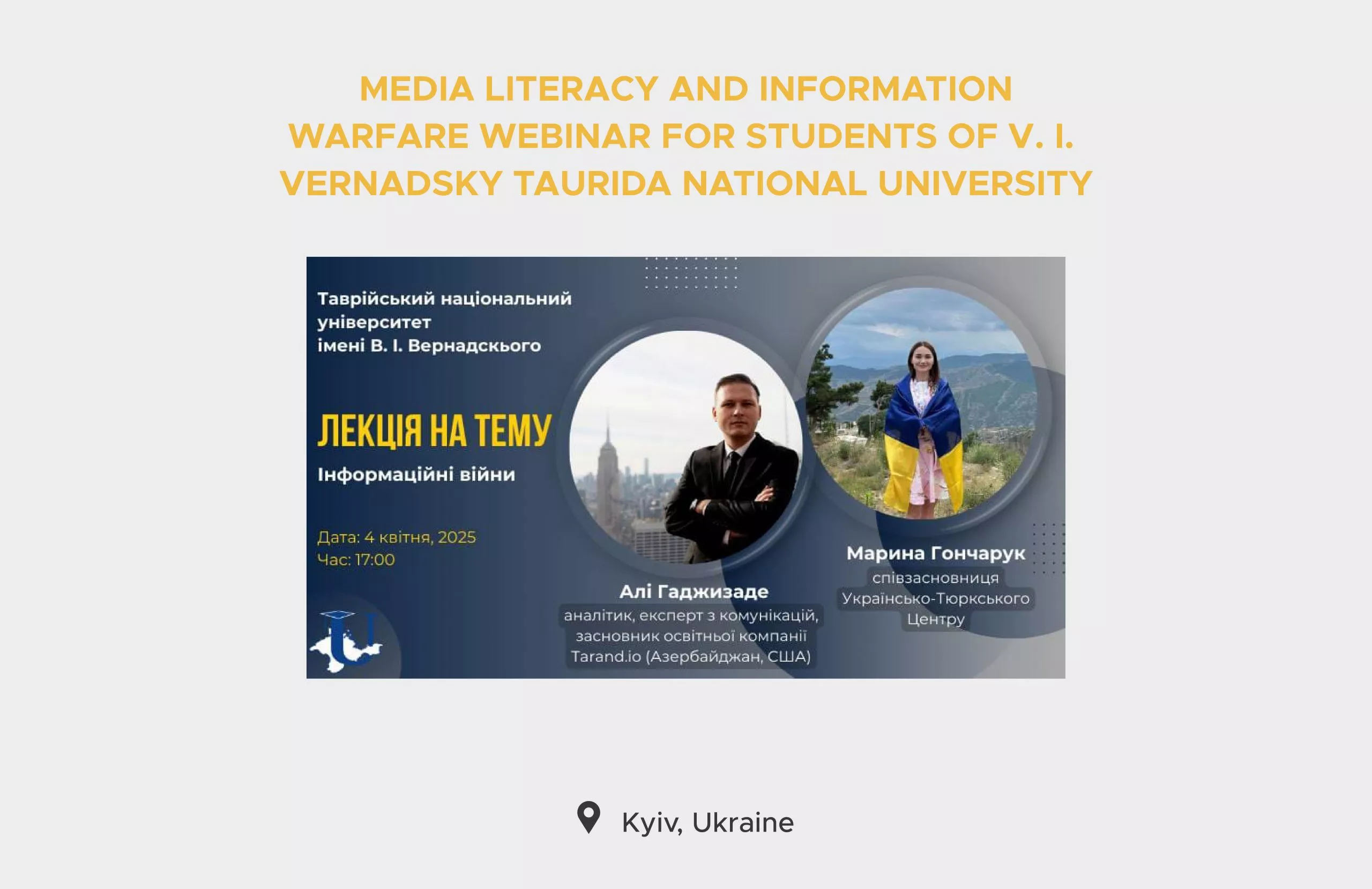
In light of the recognition of the importance for in-depth research, as well as raising awareness about such malicious information activity, Tarand experts developed a comprehensive online training on Russian propaganda and information operations.
Understanding the nature, goals, and methods of Russian malicious information activity can facilitate the understanding and identification of Chinese and Iranian malicious information activities too.
In 2023, as in previous years, the United States will continue to face the risks that stem from malicious information activity by non-state actors. These parties could be from within the United States and beyond the country’s borders. As in the past, their situational or long-term alliances and coordination of activities with the major malicious actors (Russia, China, Iran) are not ruled out.
Major malicious actors have and continue to take advantage of gaps in legislation, as well as prey on the vulnerabilities of European democracies. A fairly effective network has been created within NATO countries, which shows how entrenched these malicious operations have become. This network is part of the systematic agenda for global confrontation with the United States and poses a significant threat to US information security.
It is clear that in 2023, Washington will need to work closely with European partners, including their NATO allies, to expose proxy agents recruited by Russia, Iran, and China.
Continued activity and growing interest of malicious actors in the Caribbean and South America is a grave concern. In the event of a massive increase in anti-American rhetoric from information activity in these countries, malicious actors may open an all-out southern information front against the United States.
Millions of migrants from these aforementioned regions, who reside in the U.S, either legally or otherwise, may be susceptible to “charged” information products created in their own native languages & spread in their home countries, which may likely cause problems as well as provide additional operational advantages for malicious actors.
Despite the increased regulation & tightening of control by major social networks, there is still an ample room for the activities of malicious actors there.
Malicious actors are constantly improving their disguise techniques, subtly spreading narratives and conspiracies with their methods, thereby complicating the identification of this content by the social networks.
The use of artificial intelligence in information warfare is growing more prevalent. The rise of AI efficiency in creating deep fakes, generating texts, etc., entails new risks in the field of human-focused information security, as it facilities the efforts of malicious actors and allows them to significantly amplify their activities at low financial costs.
Whilst the right of retaliation is enshrined in International Law & US Law for conventional warfare (a physical missile or bomb strike), victims of an information attack (not to be confused with a cyber-attack) do not have the same right to retaliate according to international and US law. Therefore, being proactive rather than reactive is the best policy for this type of “warfare.” Constant analysis and monitoring of all malicious information activity that could pose direct or indirect threats or challenges to US national security is thus highly important and critical.
Of course, the human-focused information security challenges that the United States will face in 2023 are much more extensive and could be the subject of a larger report. But we decided just to briefly touch upon this topic in our first publication of the year.