Insider threats arise when people with legitimate access. Employees, contractors, or partners – use (or lose) that access in ways that harm the organization. U.S. guidance converges on this point: the Cybersecurity and Infrastructure Security Agency defines an insider threat as the potential for an insider to use authorized access or special understanding to damage confidentiality, integrity, availability, people, or facilities, whether through malicious, complacent, or unintentional acts, and the NIST glossary similarly centers the definition on authorized access and resultant harm. These risks encompass misuse, errors, and the exploitation of trusted access after credential theft, which turns insiders into unwitting conduits for attackers.
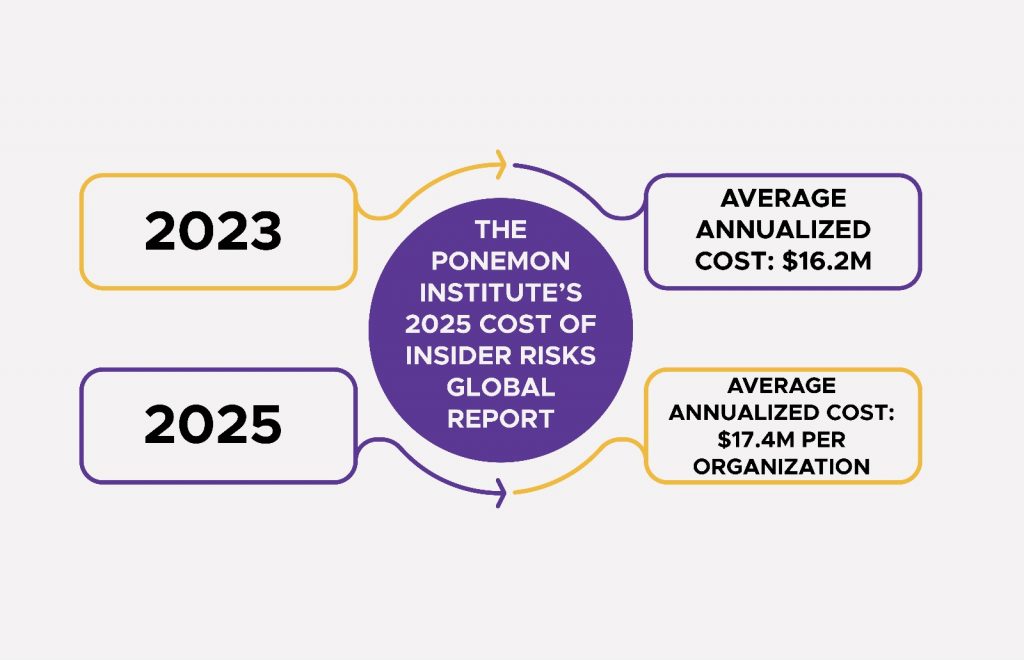
The scale of the problem is measurable and rising. The Ponemon Institute’s 2025 Cost of Insider Risks Global Report places the average annualized cost of insider risk at $17.4 million per organization, up from $16.2 million in 2023.
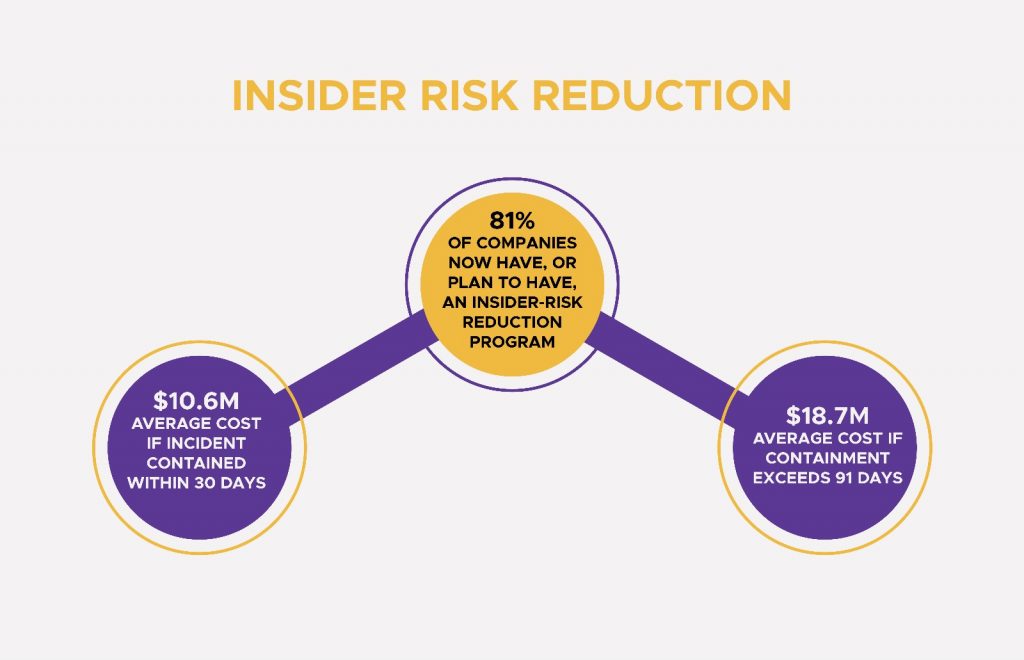
For the first time since this study began, the average time to contain an insider incident has declined to 81 days (from 86), and budgets are catching up: organizations now devote approximately 16.5% of their security spending to insider-risk management, up from 8.2% in 2023. Adoption is broad as well – 81% of companies now have, or plan to have, an insider-risk reduction program. Cost curves underscore the value of speed: incidents contained in 30 days average about $10.6M, versus $18.7M when containment exceeds 91 days.
Human behavior remains the dominant pathway. Verizon’s 2024 Data Breach Investigations Report attributes a “human element” to 68% of breaches (a metric that excludes malicious privilege misuse to focus on what awareness and controls can influence). DBIR also quantifies speed: the median time to click a phishing link after opening is 21 seconds, and only another 28 seconds to submit data – meaning a misstep can become a compromise in under a minute. Sectoral patterns vary: in healthcare, where many staff touch sensitive data daily, internal actors account for 70% of breaches (versus 30% external), and errors such as misdelivery remain a persistent exposure.
Recent cases illustrate the range of insider scenarios. In 2023, Tesla disclosed that two former employees leaked files to a German outlet, exposing personal data on more than 75,000 current and former workers; the company filed suit and notified regulators. In U.S. retail brokerage, Cash App Investing reported in April 2022 that a former employee downloaded internal reports after termination, ultimately affecting approximately 8.2 million customers. At the other end of the spectrum, insider threats also include trade-secret theft. In March 2024, a former Google software engineer was arrested and charged with stealing AI-related trade secrets while allegedly working with China-based firms. Earlier, Canada’s Desjardins breach demonstrated how long-running insider exfiltration can escalate in impact: regulators concluded that a combination of administrative and technical gaps enabled a breach affecting 9.7 million people.
What reduces insider risk is a mix of governance, access hygiene, monitoring, and behavior change. A cross‑functional program with executive sponsorship, bringing together security, HR, legal, and privacy, should align with recognized control catalogs such as NIST SP 800‑53 to embed least‑privilege access, auditable activity, separation of duties, and effective offboarding. CISA’s Insider Threat Mitigation Guide offers an actionable framework for defining, detecting, assessing, and managing insider risk in organizations of varying sizes and maturity levels. Operationally, that translates to routine entitlement reviews for high‑risk roles; immediate credential revocation and device/application key disablement at separation; segmentation and encryption around “crown‑jewel” data; and analytics such as DLP and UEBA to baseline normal behavior and flag anomalies (e.g., mass file copies, unusual queries, or policy‑evading compression).
Training is the lever that measurably bends the curve on negligent and “outsmarted” insider scenarios. Large benchmarking datasets show that sustained programs can drastically reduce susceptibility; for example, KnowBe4’s 2025 Phishing by Industry Benchmarking Report reports an 86% drop in global “phish‑prone” rates after 12 months of continuous training. Expert guidance also cautions against unrealistic targets. SANS notes that aiming for a 0% click rate is not only unattainable but potentially counterproductive, as people make mistakes, and the goal is risk reduction rather than perfection. Training should therefore be continuous, scenario‑based, and paired with rapid detection and response. Ponemon’s cost analysis indicates a practical containment objective of under 30 days, where total costs are markedly lower than in long‑dwell incidents.
In sum, insider threats persist because organizations must grant people access to valuable systems and data; that necessity, not malice alone, creates exposure. The evidence points to a durable combination: transparent governance, least‑privilege access with fast offboarding, continuous monitoring with analytics and segmentation, and training that changes day‑to‑day behavior. Costs are still rising, but time‑to‑contain is falling where insider‑risk programs are mature, and well‑designed awareness at scale markedly reduces the likelihood that errors or stolen credentials turn into major incidents. Investing in ongoing training and sustained monitoring is therefore not a checkbox exercise but the core of a living risk‑reduction program. Leaders should revisit metrics quarterly and adjust controls as roles, vendors, and threat tactics evolve.